Using Configuration Masters to Centrally Manage Web Security Appliances
Your Security Management appliance provides different versions of Configuration Masters, so that you can centrally manage your Web Security appliances. Each Configuration Master supports multiple sub Configuration Masters under it. The sub configuration masters allows you to define different policy configurations within the same configuration master.
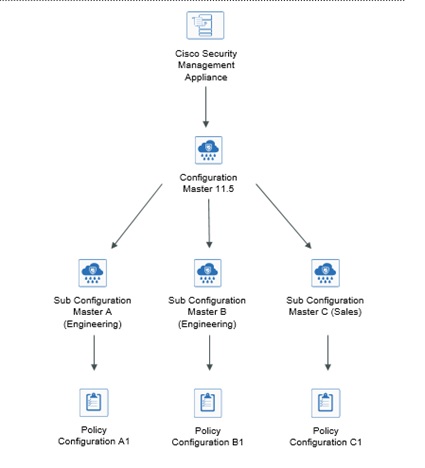
Assume that your engineering and sales teams are using AsyncOS 11.7 for Web Security appliances. Your organizational policy requires you define different policies for these teams. In this scenario, you can create two sub configuration masters under the Configuration Master 11.7 and define different policy configurations for each sub configuration master, as shown in the following figure:
Note | The current version of Cisco Configuration Master does not fully support simultaneous access by multiple users. If one user is applying changes to a configuration master while another is switching between configuration masters, unexpected impacts may occur. The changes made by the first user can affect the configuration master that the second user switches to, potentially leading to issues once changes are published to the WSAs. To avoid conflicts or unexpected behavior, it is recommended to:
|
Setting Up Configuration Masters to Centrally Manage Web Security Appliances
The following table provides instructions to initialize and configure Configuration Masters and sub configuration masters.
|
Steps |
Do This |
On This Appliance |
More Information |
|---|---|---|---|
|
Step 1 |
Check for general configuration requirements and caveats. |
— | |
|
Step 2 |
Determine the Configuration Master version to use for each Web Security appliance. |
— | |
|
Step 3 |
On all target Web Security appliances, enable and configure the features and functionality that are required to support the policy and other settings that you will configure in Configuration Masters on the Security Management appliance. |
Web Security appliances |
— |
|
Step 4 |
(Optional) If you have a working Web Security appliance that can serve as a configuration model for all of your Web Security appliances, you can use a configuration file from that Web Security appliance to speed configuration of a Configuration Master in the Security Management appliance. |
Web Security appliance |
For instructions on downloading a configuration file from a Web Security appliance, see “Saving and Loading the Appliance Configuration” in the AsyncOS for Cisco Web Security Appliances User Guide. |
|
Step 5 |
Enable and configure Centralized Configuration Management. |
Security Management appliance |
See Enabling Centralized Configuration Management on the Security Management Appliance. |
|
Step 6 |
Initialize the Configuration Masters. |
Security Management appliance | |
|
Step 7 |
(Optional) Configure Sub Configuration Masters |
Security Management appliance | |
|
Step 8 |
(Optional) Select the Sub Configuration Master as the Active Configuration |
Security Management appliance |
See Selecting the Sub Configuration Master as the Active Configuration |
|
Step 9 |
Associate Web Security appliances to the Configuration Masters. |
Security Management appliance |
See About Associating Web Security Appliances to Configuration Masters. |
|
Step 10 |
Import and/or manually configure policies, custom URL categories, and/or a web proxy bypass list in the Configuration Masters. |
Security Management appliance | |
|
Step 11 |
Ensure that the features enabled on each Web Security appliance match the features enabled for the Configuration Master assigned to that appliance. |
Security Management appliance | |
|
Step 12 |
After you have set up required Configuration Masters and enabled appropriate features, publish configurations to your Web Security appliances. |
Security Management appliance | |
|
Step 13 |
Prepare in advance for possible URL Category set updates that can modify your existing Configuration Master settings. |
Security Management appliance |